Zero Knowledge Proofs (ZKPs) are gaining traction in today’s tech landscape, particularly in blockchain and Web3 sectors. The rise of Zero Knowledge-based public chains, zkRollups and zk based dApps are notable, but it’s important to remember that ZKPs can also be applied outside of blockchain as well. The primary appeal of ZKPs are enhanced privacy and improved scalability, and they can be applied in a multitude of sectors.
Essentially, ZKPs allow users to access personalized web services while keeping their private information secure, along with the benefit of reduced amount of data that needs to be processed.
In this article, we will explore various practical applications of ZKPs, with or without blockchain, showing how they contribute to the development of more privacy-friendly, scalable and efficient products for businesses across sectors.
What are ZKPs?
ZKPs or Zero-Knowledge Proofs are cryptography primitives that use mathematical computations to provide only the information required to validate a question without revealing the entire information.
Let’s break the core ideas of ZKP with a simple example.
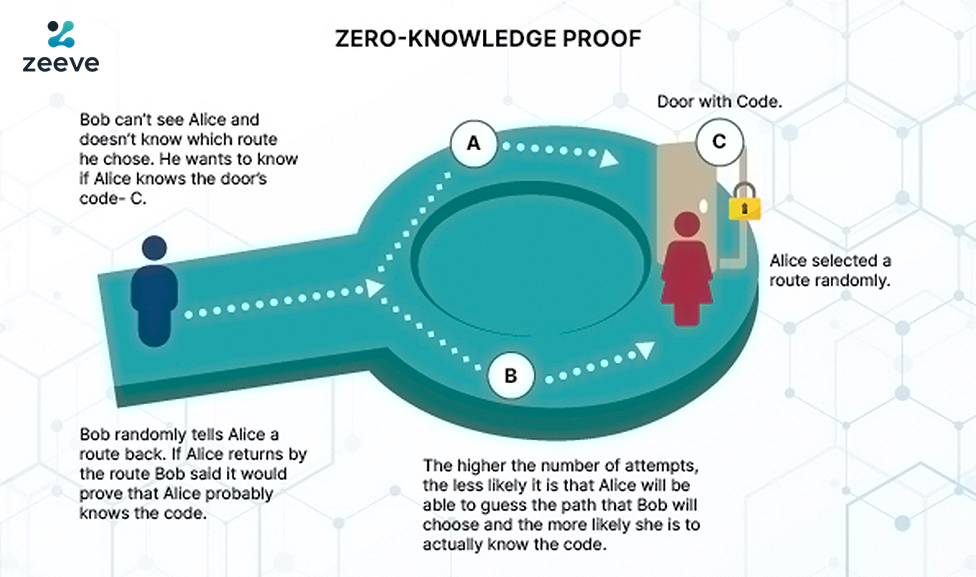
Imagine Alice needs to show Bob she knows a secret passkey without actually telling him what it is. They’re at this circular cave with two doors, A and B, and a secret door C in the middle. The catch? Door C only opens with the passkey. So, Alice goes in through A and if she pops out of B, Bob gets the message – she knows the secret without her saying a word.
The more times she does it, the less likely she’s just guessing. It’s like a trust game, proving she’s in the know, perfect for blockchain stuff where trust is key but secrets are too.
For those interested in the nuts and bolts of how ZKPs function and their complex underpinnings, feel free to dive deeper into our detailed blog post where we unwrap the layers of this fascinating subject:
What are Zero-Knowledge Proofs and why are they important for blockchain?
Practical Application of ZKP Across Different Stakeholders
Helping Government In Maintaining Democracy
Though elections have been the greatest testament to validate the dance of democracy, the outcomes have failed to reach its true potential. Why? Because, there’s no true mechanism in place that can validate the exercise of franchise.
That’s why in the past, most of the time the authenticity of the voting has been questioned. And such occurrences add insult to the injury when people waste considerable time waiting in queue to cast their vote.
It is estimated that such practices cost a whopping $1 billion in productivity to the public exchequer.
In this regard, ZKP applications resolve the problem of rigging in voting through a privacy preserving, smart-contract triggered check and balance mechanism. The voters can anonymously cast their votes without revealing their true identity and the cryptography computations ensure that results could be verified on-chain to restore the true essence of democracy.
Estonia has already deployed the POC as a pilot project and it has delivered unprecedented outcomes. Voters could easily vote from the confines of their home and since the ZKP technology is fast and cheap, this could be the beginning of new discovery in making elections truly democratized, verifiable and cheap.
Countering MEV Scam
MEV or Maximum Extractable Value is another major point of failure where applications of ZKPs could solve a major reputation crisis. Why do we say that? Because, the main aim of introducing decentralization was to reestablish transparency, validation and security; however, when certain news inundate social platforms like miners/validators indulging in unethical practices to fraud users, the need for a solution arises.
Sandwich attacks, front-running and back-running transcations have triggered the necessity for a completely anonymous validation with no sharing of information whatsoever.
ZKP applications, though not in equivalence to be called as a magic bullet, nonetheless have provided a completely privatized way to deal with MEV scams. Most exchanges have been using this to protect equity tokens from abuse at the hands of the miners and sequencers in PoW and PoS consensus systems.
Protecting Financial Services Against Data Breaches
Ever since digitization has turned mainstream, it has undoubtedly exposed key vulnerabilities because financial services are heavily centralized which makes them a sitting duck for raids.
For example, in 10 of the biggest data breaches, more than 1 billion customer’s data has been put under attack. The stakes are high with respect to reestablishing trust and finserv like banks have voiced their intention to use next gen cryptographic technologies to protect against financial frauds. In this regard, ZKPs have unequivocally shown an optimistic way forward.
For example, ING, the Global Dutch Bank has been using ZKP Range Proof Functions for processing the mortgage applications. Along with ING, BBVA is also exploring the efficacies of the ZKP applications to help ensure privacy preserving transcations while using the financial services. In this way, they wish to grant true security and protection to its users who have been exploited by the hackers and frauds for sharing their private information. These frauds have taken the shape of card cloning to identify thefts to lure and cheat customers.
Scaling Blockchains For Enterprise Grade Adoption
Imagine a situation where enterprises are using blockchains and suddenly there’s some cryptokitty moment trying to sabotage the network. At that juncture, all the applications which are hosted on blockchains to support enterprise applications would cease to function. That’s the performance hiatus which is widening with time as blockchain adoption turns mainstream.
For example, in one of the surveys conducted, 18.2% sided with ZKPs in terms of providing efficiency, affordability and optimizing performance while using blockchains by enterprises. So, there could be an option where a segment of transactions or light client demands could be moved off-chains and security can be inherited from the main chain and L1’s for promoting even higher TPS and lower latencies while using the network.
That’s the reason the founder of Ethereum Vitalik Buterin said that despite the Ethereum Network unrolling sharding, we still need the ZK-roll ups to scale up to 100,000 TPS. ZK-rollups optimistic and Zero Knowledge proof systems would be the answer to fix the blockchain trilemma which has been delaying adoption in volumes by enterprises.
Also Read: Top 10 Zero-Knowledge projects of 2023
Facilitating Verifiability of Carbon Credits in Energy Sector
After assessing the possibilities of melting of the polar caps that could ideally put the world in jeopardy, the Kyoto Protocol mandated the use of Carbon Credits for developed and developing countries to restrict the emissions levels. However, the selling of fake carbon credits has been baked so hard into the systems that it is very hard to authenticate trusted vendors in a truly private way. ZKP applications have shown a way out.
Senken’s decentralized carbon marketplace allows end-to-end accountability of authentic carbon credits that solves the innate problem of duplicate carbon credits. Moreover, since the platform uses ZKPs, enterprises can verify the carbon credits they are buying privately and organizations can also post their carbon consumption, emission and saving. Thereby simplification of validation has helped enterprises post all their developments in using green technologies for Net Zero Emission.
Over 100 high quality carbon projects have been associated with Senken because right now the demand to reduce carbon emission stands at a whopping 420 billion metric tonnes; however, the supply-side has been dwarfed at 400-million tonnes because buyers have challenges validating carbon credits due to carbon market crimes which is hurting genuine sellers. Through ZKP applications, the buyers and sellers can interact on the carbon market privately to fill up this gap.
Safeguarding IoTs To Prevent Hacking of Smart-Homes and Cars
As our lives are getting smarter day-by-day to attract even greater conveniences, we have unintentionally exposed key points of failures in the process. How? For example, we boast of smart-homes but data packets traveling from one device to another can be compromised midways. The question to raise here is do we have an evidential proof for the same. As per Kaspersky, IoTs have been going through a rough phase because hackers are trying to sneak into the systems.
They use the WiFi network which acts as a key vulnerable segment acting like sitting ducks for raids as per a statistical data analysis. But, ZKP applications could right up front solve the problem of validating passwords and other details in a completely anonymous way to safeguard users.
Restoring Trust in Supplychain For Interoperability With Partner Networks
Counterfeiting, theft and delays are just the tip of the iceberg when we assess the challenges in the supplychain network. The real problem that supplychain has to go through is inability to transaction freely with the partner network. Why? Because, all the partner networks have different business secrets, operational processes and growth models that they do not want to share with others in the network.
These legacy challenges create barriers around the supplychain network which can impact the growth of the economy. ZKPs can help enterprises share data privately and in a scalable manner. In this way, it can make auditing simple, verifiable and secure. Thereby optimizing the supply chain network to meet its desired outcomes in a truly private, secure and decentralized manner.
Wrapping Up:
Zero-Knowledge proofs undoubtedly provide an extra layer of security and privacy that users are seeking to stay in-control in a highly charged digital world .
Through ZKP applications, security, privacy and scalability all could be there in continuum and with absolute perfection despite the technology being very new to be implemented. It will be interesting to see how ZKP applications further improve the efficiency of sectors across a broad spectrum as they enjoy absolute adoption 2 to 5 years down the line.
If you are looking to build an application that needs to leverage a Zero Knowledge Proof public chain, check out Polygon zkEVM and zkSync Era on Zeeve. If you need your own custom ZK powered chain, check out our zkRollups-as-a-Service solutions. It enables you to launch a zkRollup in a low code way using Polygon CDK.
If you have any query, talk to our Zeeve experts and see how we can simplify your Zero Knowledge journey.