In our previous article, “Introduction to Institutional Staking: A Business Guide,” we provided a comprehensive overview of staking, covering its fundamental principles, the unique aspects of institutional staking, the growing interest in this field, and the staking rewards offered by various popular blockchains.
Building on that foundation, in this blog, we will shift our focus to mitigating the risks associated with institutional staking. By understanding and addressing these risks, we can ensure a secure and successful staking experience for institutional investors.
Let’s explore the key risks in institutional staking and the strategies to mitigate them effectively.
Key Risks in Institutional Staking
Like any investment vehicle, staking comes with its own set of risks. The major risks in staking are:
- Custody Risks
- Maintenance Risks
- Slashing Risks
- Other Considerations
In the subsequent sections, we will delve into each of these risks, discussing their implications and exploring strategies to mitigate them effectively.
1- Custody Risks:
When it comes to custody risks in institutional staking, one crucial consideration is how the assets will be managed. This decision involves choosing between utilizing a custodian who will have full control over your assets or opting for a non-custodial solution where you retain management of your private keys.
With custodial solutions, the main risk lies in the fact that a third party gains some level of access to your assets. While this can provide convenience, it also raises concerns about the security and control of your assets, as you are relying on the custodian’s infrastructure and security practices.
On the other hand, managing the assets yourself requires not only the necessary knowledge but also robust security protocols to ensure that you do not lose access to your assets or fall victim to any theft or hack.
There is a type of staking available that involves transferring or delegating your assets completely to a third party who will then stake on your behalf. Here your funds are mixed with those of other participants and a staking pool is formed. It can often offer a more cost-effective approach.
However, it is essential to note that custodial platforms in the crypto industry tend to charge higher fees compared to traditional finance, with fees typically around 20% rather than 2%. This significant difference can present a significant barrier to entry for institutional investors. While regulations in developed countries have imposed certain safeguards to mitigate the risk of custodial platforms running away with funds, custody still carries inherent risks that demand careful consideration and organization of assets.
2- Maintenance Risks
Maintenance risks are a significant consideration in institutional staking, as blockchain networks are not a “set and forget” kind of infrastructure. These networks undergo continuous changes, including upgrades to the underlying software, network modifications, and security patches, necessitating validators to remain updated in order to avoid potential expulsion from the network.
Learn more on validator Nodes: Everything you need to know about Validator Nodes: a deep dive
When engaging in staking, it becomes crucial to maintain maximum uptime to capitalize on the potential returns on your capital. Any disruption or downtime can result in lost opportunities or reduced rewards. Furthermore, the risk of losing access to your assets due to code exploits or missing out on returns during network updates adds to the complexity of maintenance risks.
3- Slashing Risks
Institutional staking carries inherent slashing risks due to the penalty mechanisms employed by PoS protocols. Slashing serves as an incentive for proper consensus and acts as a deterrent for malicious or irresponsible behavior within the blockchain network.
Active network participants function as whistleblowers, detecting and reporting rule violations by constructing infringement statements in new blocks. When a validator is found guilty of misconduct, they face penalties, which can include the invalidation of their validator ID and monetary fines. The severity of the penalty depends on the number of validators involved, with a larger number resulting in higher penalties.
As a form of incentive, whistleblowers receive a portion of the collected penalties as a reward.
In the subsequent sections, we will delve into the two behaviors (Downtime &
Double signing) that commonly trigger slashing:
- Downtime:
Downtime is a crucial risk to consider in institutional staking, occurring when a validator is offline and unavailable to fulfill its responsibilities when called upon by the blockchain. During such periods of downtime, validators miss out on the opportunity to validate transactions and consequently forfeit the rewards they would have received.
Consistent and prolonged downtime can result in penalties, where validators may be required to forfeit a small portion of their staked tokens, typically around 0.1% of the stake. This penalty system incentivizes validators to maintain consistent uptime and active participation in the network.
To mitigate the risks associated with downtime, investors who lack technical expertise may opt to utilize public validators instead of becoming dedicated validators themselves to minimize the potential impact of downtime issues. Though, utilizing public validators come with a revenue-sharing arrangements that can affect the overall profitability of staking.
- Double Signing:
Double signing is a serious risk in institutional staking that occurs when a validating entity, typically associated with a private key, submits two signed messages for the same block. This situation can arise when a node operator or infrastructure provider optimizes their node configuration by having a highly available backup entity running concurrently with the primary entity to prevent downtime.
However, double signing is considered a much more significant offense compared to downtime, resulting in substantially larger penalties. The penalties for double signing can be as high as around 5% of the stake, reflecting the severity of the violation.
To mitigate the risk of double signing, it is crucial for validators to implement robust measures and ensure proper synchronization between primary and backup entities.
4- Other Considerations:
- Setup & Educational Time:
Each blockchain needs a separate node. Managing and maintaining multiple nodes for staking across different blockchain networks can be challenging and time-consuming. Each blockchain has its own requirements and learning curves, making it inefficient and impractical for institutions to develop in-house expertise for every network. This setup and educational time can pose a significant hurdle for institutions looking to engage in staking businesses.
- Cost Analysis:
Building and maintaining a staking system can entail substantial costs. These costs include hardware, infrastructure, security measures, and ongoing maintenance expenses. Institutions need to conduct a comprehensive cost analysis to determine if the potential returns from staking justify the associated expenses. The rapidly evolving nature of the staking landscape adds an additional layer of complexity to cost analysis, making it important to carefully assess the cost-effectiveness of institutional staking.
If you are interested to dive deep into the cost of doing blockchain, explore this GBA Webinar, presented by Ghan Vashishtha , cofounder & CTO of Zeeve.
GBA Webinar – Episode 1 “Enterprise Blockchain Adoption” – Cost of doing blockchain – Zeeve
- Unbonding Periods:
Staking involves periods during which staked tokens are locked and unavailable for sale or immediate use. These protocol-enforced unbonding periods can vary in duration, ranging from hours to weeks, depending on the specific token and network. Institutions need to consider these periods of illiquidity and account for them in their liquidity management strategies and overall financial planning.
- Jurisdiction risks:
Institutions must equally pay due importance to analyzing where they want to stake their crypto assets. For example, the European Union has passed the MiCA bill which aims at safeguarding investors interest. Under the MiCA legislation, one has to provide all the details that could avoid possibilities of money laundering. Hence, if you are wishful of pursuing institutional staking, in that case, you have to keep that in mind.
What Options Enterprises have for Staking?
Enterprises exploring staking opportunities have primarily 4-options to consider. These options range from self-hosted solutions to custodial services, liquid staking, and white-labeled validator nodes. Each option presents distinct advantages and considerations, catering to different institutional requirements and preferences.
- Go self-hosted:
When choosing to go self-hosted, enterprises take on the responsibility of managing their own staking infrastructure, providing them with complete control over the staking process.
However, this decision requires careful consideration and strategic planning. It involves building an in-house team with the necessary technical expertise and making substantial investments in the required infrastructure.
Security becomes paramount as validators need to protect against malicious attacks, including distributed denial-of-service (DDoS) attacks, and ensure 100% uptime.
If an enterprise intends to become a validator across multiple blockchains and treat staking as a business, choosing a self-hosted approach can be counter productive sometimes.
While it solves custody risks by eliminating reliance on third-party custodians, it does not eliminate maintenance risks, slashing risks, and other considerations discussed earlier. Ongoing responsibilities for maintenance, uptime, and mitigating risks still apply.
- Use Custodial / Delegation Services:
Custodial solutions or delegation offer a relatively straightforward solution for institutional staking.
By opting for custodial solutions, institutions can rely on third-party providers to handle the custody of their staked tokens. Furthermore, there is a risk of third-party data breaches, highlighting the importance of selecting reputable and secure custodial service providers.
Alternatively, institutions may choose to delegate their tokens to validators instead of becoming validators themselves. This delegation route allows institutions to earn rewards based on the delegated stake percentage. However, it is crucial to conduct thorough research and due diligence when selecting validators to ensure their reliability, track record, and adherence to protocol rules.
This option addresses the major concerns of slashing, maintenance risks, and certain points in the “Other Considerations” section. However, choosing custodial solutions or delegation dilutes the level of custody control, as third-party providers handle asset security.
- Liquid Staking: A non-custodial, smart-contract way
Liquid staking is a relatively new staking service that gained adoption in 2022, driven by the growing popularity of DeFi products. . This allows users to directly stake their assets on a proof of stake network(in a staking pool), such as Ethereum, while simultaneously receiving a programmatically minted liquid staking token (LST). The LST provides users with access to liquidity, allowing them to utilize their staked assets while still earning staking rewards. The staked funds are stored in an escrow account to ensure security.
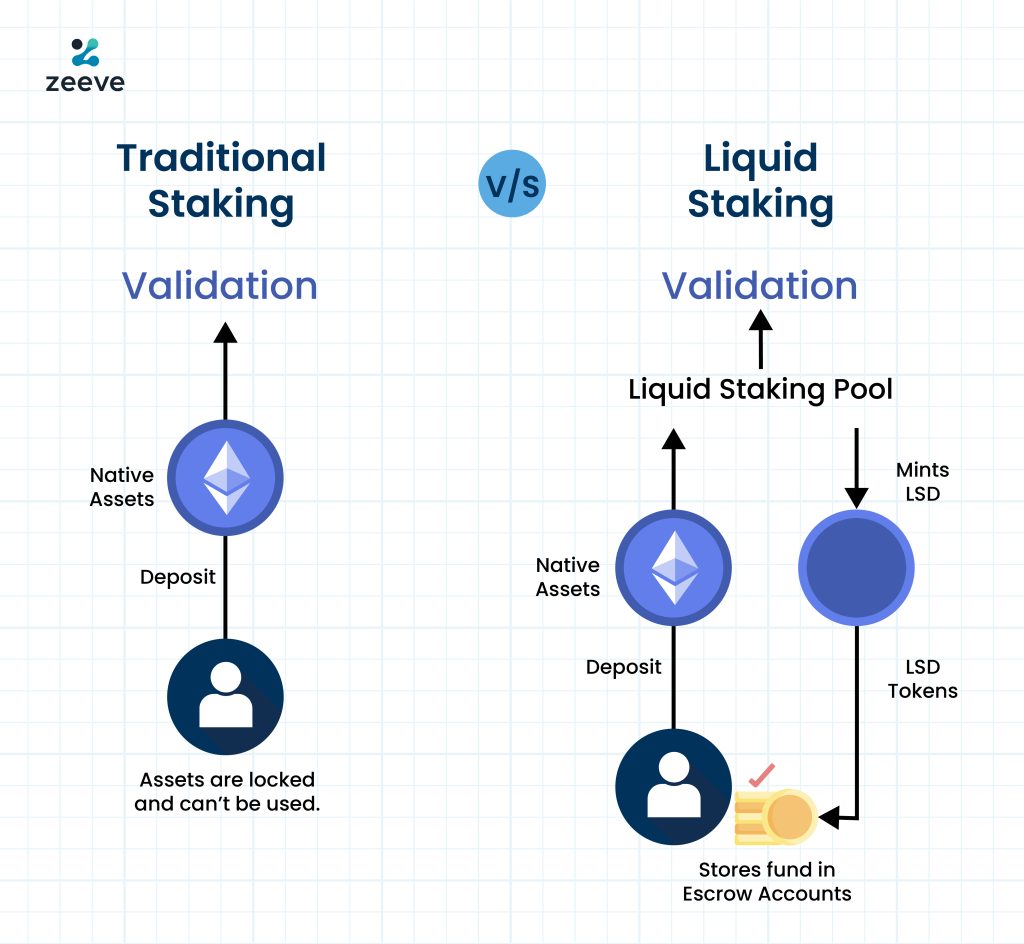
However, it’s important to be aware of the risks associated with liquid staking. One risk is the potential depegging of the LST tokens from the original staked tokens, which can result in loss of value. Additionally, there is a risk of losing the LST tokens themselves, as they are typically held in smart contracts. Smart contract bugs or exploits could also potentially lead to the loss of user funds.
While staking carries inherent risks, it does not subject investors to impermanent loss or pose concerns related to smart contract and oracle risks. But in case of Liquid Staking, it does. Therefore, it is crucial for users to exercise caution and conduct thorough research when participating in liquid staking services.
- Use White-labeled Validators:
White-label validator nodes are another feasible option available to Institutional investors. This approach involves partnering with a reliable third-party provider who offers the validator nodes infrastructure and expertise. The key advantage is that institutions retain full control of their nodes while benefiting from a fully non-custodial solution that aligns with the specific benefits offered by the targeted blockchain.
White-label nodes present a viable option for mitigating slashing related risks in institutional staking with guaranteed near 100% uptime. They effectively self-manage the infrastructure without taking control of the private keys, eliminating concerns related to slashing and downtime.
Additionally, if permitted by the blockchain protocol, institutions can accept delegations from others. They have the freedom to decide the delegators’ reward percentage, choose the preferred address for receiving block rewards, and also consider options like whether to reinvest the rewards along with the principal amount or not for compounding benefits.
By opting for white-labeled validator nodes, institutions can redirect their focus towards core activities, delegate infrastructure management, and enjoy the full benefits offered by the blockchain for validators while maintaining complete control over their assets.
Why Zeeve For your White-labeled Staking Nodes?
Enterprise-grade staking requires not only reliable infrastructure but also the expertise and support behind it.
At Zeeve, we offer a comprehensive range of services tailored for your enterprise-grade staking nodes. Here’s what sets us apart:
- Enterprise-Grade Security: Our dedicated team of experts provides 24/7 security monitoring and deploys robust security tools to safeguard your staking node. With our enterprise-grade infrastructure, we ensure that your staking operations remain secure and protected.
- Uptime Guarantee: We prioritize uptime by implementing multi-layered proactive monitoring. Our vigilant monitoring systems ensure that your validator node remains active and operational, minimizing any potential downtime.
- Non-Custodial Solution: With Zeeve, you retain full control over your dedicated staking node while we handle the underlying infrastructure. This non-custodial approach empowers you to have complete authority and access to your assets.
- Extensive Network Support: We offer support for over 35 Proof-of-Stake (PoS) networks, including established blockchains and newer ones such as Shardeum, Aptos, Coreum, DCOMM, Near, and many more. Our infrastructure combines bare metal hardware with a global network of nodes hosted across multiple geographical locations.
- Compliance with Industry Standards: Zeeve adheres to ISO and SOC2 Type II standards, ensuring the highest level of security and data privacy. We are also GDPR compliant, prioritizing the protection of your sensitive information.
If you are interested in white-labeled staking or would like to learn more about Zeeve’s role as a validator service provider, please connect with us.
Discover how Zeeve can simplify your non-custodial staking experience, providing you with a hassle-free solution tailored to your needs.