Digital algorithms, commonly referred to as hash values, are outcomes of cryptographic hash algorithms, which are mathematical protocols that can manipulate data of indefinite length. The domains of cryptography, cyber security, and data integrity validation heavily depend on these hash algorithms.
Cryptographic hash algorithms are beneficial for verifying the genuineness of digital data through the digital signatures they generate. Cryptographic hash algorithms furnish a singular hash value for each data element, allowing for detecting even the slightest modifications in the data, signifying tampering or degradation.
In this article, we delve into the subject of cryptographic hash algorithms, exploring what they are, their functions, and some common applications. We shall also delve into the need to enhance cryptographic hash algorithms to prevent weaknesses and the security of cryptographic hash algorithms, particularly their ability to resist collision and preimage attacks.
Hash functions in cryptography: Their Defining Features
One subset of hash functions, known as cryptographic hash functions, is developed to include additional security features.
- Determinism: Given the same input, a cryptographic hash function will always provide the same result. Hash functions are also collision-resistant, meaning there will not be two same outputs for two different inputs.
- Non-invertibility: It is computationally impossible to recover the original input from the hash value. So, it can’t be reverse-engineered. Given the importance of maintaining data integrity, cryptographic hash functions find widespread use in digital signatures and other such systems.
- Input Size Independent: No matter the input size, all cryptographic hash algorithms will always provide the same length hash result. This facilitates the comparison of hash values and the identification of data modifications.
- Avalanche effect: Even little changes to the input data will result in a significantly different hash value. This ensures that any alterations to the original data can be immediately identified, which is very important.
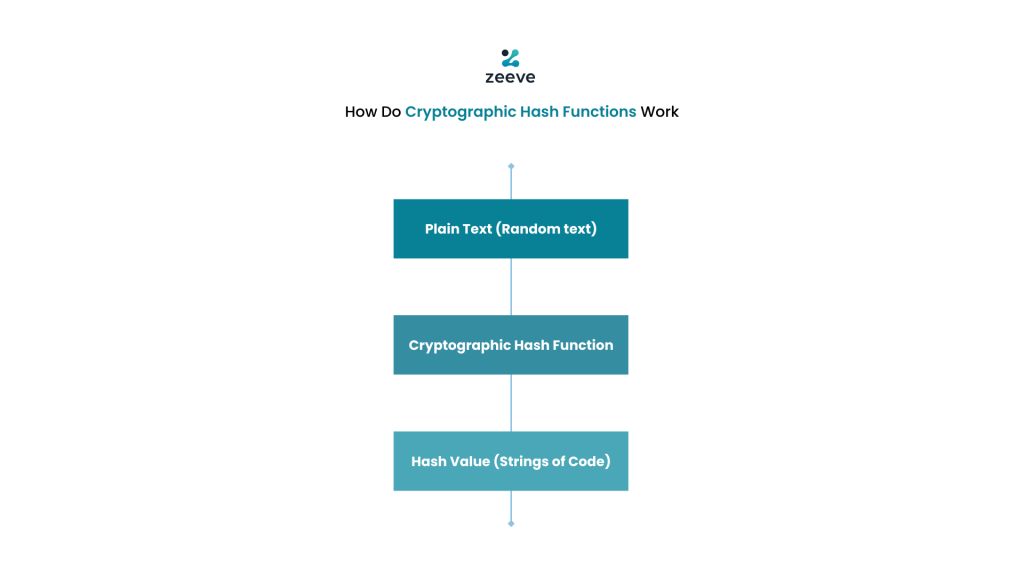
How Do Cryptographic Hash Functions Work?
A hash function, also known as a message digest or hash value, is a mathematical function that takes a message as its input and produces a matter of a defined length. The same intake will always result in the same hash value since hash functions are designed to be deterministic.
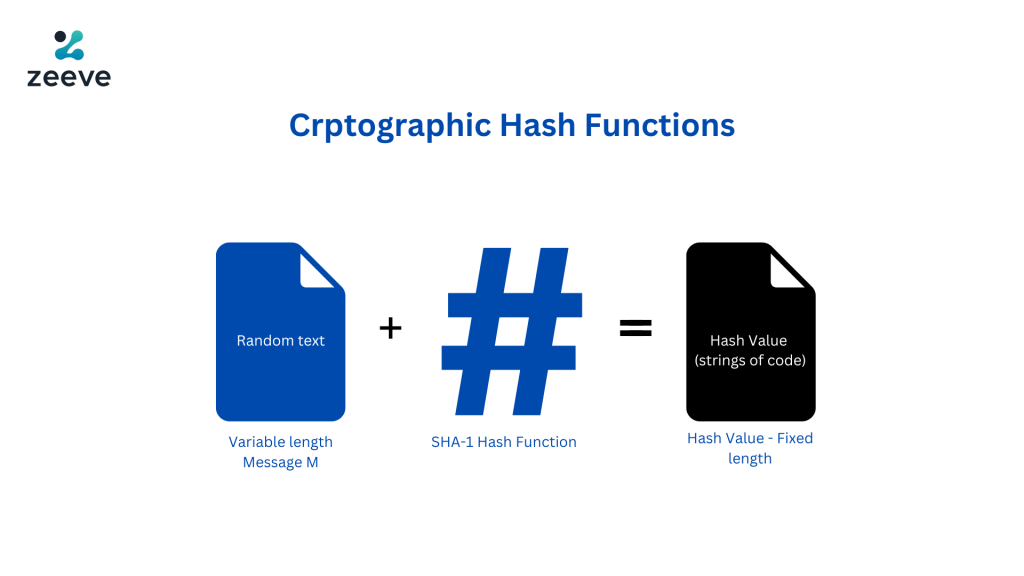
The process of hashing commences with the subject data undergoing a series of mathematical procedures comprising logical and bitwise manipulations and modular arithmetic. These methods generate a one-of-a-kind hash value specific to the input information.
Imagine a user creates an account and sets their password to “password123”. The password undergoes a cryptographic hash function, such as SHA-256, and the resultant hash value is stored in the database, for example, “5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542”.
Upon a user logging in, their entered password is subjected to the procedure of hashing and is compared to the stored hash value. If they coincide, the user is granted access. Given that the stored hash value is exclusive to the password, even if a malicious actor gains access to the database, they will not be able to determine the original password. Furthermore, the hash function guarantees that any slight alteration to the password will yield a significantly different hash value.
Salt is also employed in cryptographic hash functions to enhance security. It is a random value combined with the input information before it undergoes the hash function. This makes it challenging for attackers to discover collisions or preimages, as the salt renders it computationally impractical to create hash values congruent with the intended hash value.
Exemplary Cryptographic Hashes
Some of the most extensively employed cryptographic hash algorithms in current usage are:
SHA (Systematic Hash Algorithm)
The Systematic Hash Algorithm (SHA) is a component of the SHA class of hash functions, which was devised by the NSA and is extensively utilized in cryptography. SHA encompasses multiple diverse implementations; SHA-1, SHA-2, and SHA-3 are only a few samples.
This is the primary hash algorithm in the Systematic Hash Algorithm (SHA) category, and it is frequently applied to guarantee data integrity. Unfortunately, SHA-1’s security deficiencies indicate it has mostly been replaced with the more secure SHA-2.
SHA-2 is a class of hash algorithms encompassing SHA-224, SHA-256, SHA-384, and SHA-512, among others. The transmission of confidential information and the digital signatures’ authentication is significantly improved through these hash algorithms as opposed to the older, less secure SHA-1.
SHA-3 is the most recent revision to the SHA hash function class and was developed to rectify several security flaws with SHA-2. It is a widespread practice to utilize SHA-3 functions in a broad spectrum of contexts due to their dependability and security.
MD5 (Message-Digest Algorithm 5)
Cryptographic Hash Algorithm 5, also called Message-Digest Algorithm 5, is a well-known cryptographic hash function that Ron Rivest devised in 1991. This function processes an input of indefinite magnitude and outputs a 128-bit hash value with a fixed length, typically depicted as a 32-character hexadecimal representation.
A key characteristic of Cryptographic Hash Algorithm 5 is its aptitude to detect any alterations made to the input information, regardless of whether the modification is as minute as a single bit. This is known as the “integrity” of the data, which is fundamental in computer security. Whenever a file or communication is transmitted over the internet, its Cryptographic Hash Algorithm 5 hash is computed and sent along with it. The recipient then computes the Cryptographic Hash Algorithm 5 hash of the received information and compares it to the original hash to confirm that it hasn’t been altered during transmission.
Cryptographic Hash Algorithm 5 is also frequently utilized for password storage and authentication. When a user creates an account and sets a password, the password isn’t stored in its original form for security purposes. Instead, the password is hashed using the Cryptographic Hash Algorithm 5 technique, and the resulting hash value is stored in the database. When the user signs in, the password supplied by the user is hashed using the same technique, and the resulting hash is compared to the stored hash value to authenticate the user’s identity.
Despite widespread usage, Cryptographic Hash Algorithm 5 has demonstrated multiple vulnerabilities, including collisions, where two different inputs may generate the same hash value. This enables an attacker to create two separate messages with the same hash and bypass security measures. Due to these vulnerabilities, Cryptographic Hash Algorithm 5 is considered a weak hash function and is being phased out in favor of more robust hash methods such as SHA-256.
BLAKE 2
As a substitution for primary hash functions such as MD5 and SHA-1, the BLAKE2 family of cryptographic hash algorithms was devised. Its rapid velocity and a high degree of security make BLAKE2 an optimal selection for various applications requiring data integrity verification or the transmission of confidential information through a secure channel.
Similar to other keyed hash functions, BLAKE2 necessitates a key in addition to the message to be hashed, thereby enhancing the overall security of the hash function by providing an extra layer of protection against attacks. Furthermore, BLAKE2 can generate hash values of varying lengths, offering a wider range of options for implementation.
In cryptography and digital signatures, the hash value of a message is utilized to authenticate its origin and integrity, and this hash function is widely used for this purpose. The hash value functions as the message’s digital signature in various scenarios, permitting a foolproof verification of its authenticity and integrity before, during, and after transmission.
In terms of accessible hash algorithms, BLAKE2 is regarded as one of the fastest, making it a desirable choice for high-performance computing and large data processing where every second counts.
RIPEMD
A European substitute for vulnerable hash methods such as MD5 and SHA-1 is the RIPEMD family of hash functions. Various RIPEMD implementations produce hash values of differing lengths, with RIPEMD-160, RIPEMD-256, and RIPEMD-320 being a few examples.
To authenticate digital signatures and guarantee data integrity, cryptographers often employ RIPEMD as a hash function. As the RIPEMD hash value serves as a digital signature of the message, it can be utilized by the recipient to confirm that the message was transmitted in its unaltered form and has not been subjected to tampering.
One of the most remarkable qualities of RIPEMD is its resistance against attacks. The hash function exhibits fortitude against several assaults, including collision attacks and preimage attacks. It is optimal for applications where security is of paramount concern, such as confidential communication and financial transactions.
The versatility of RIPEMD stems partly from its ability to generate hash values of any length. Applications, where space is at a premium may greatly benefit from this as a smaller hash value may be utilized.
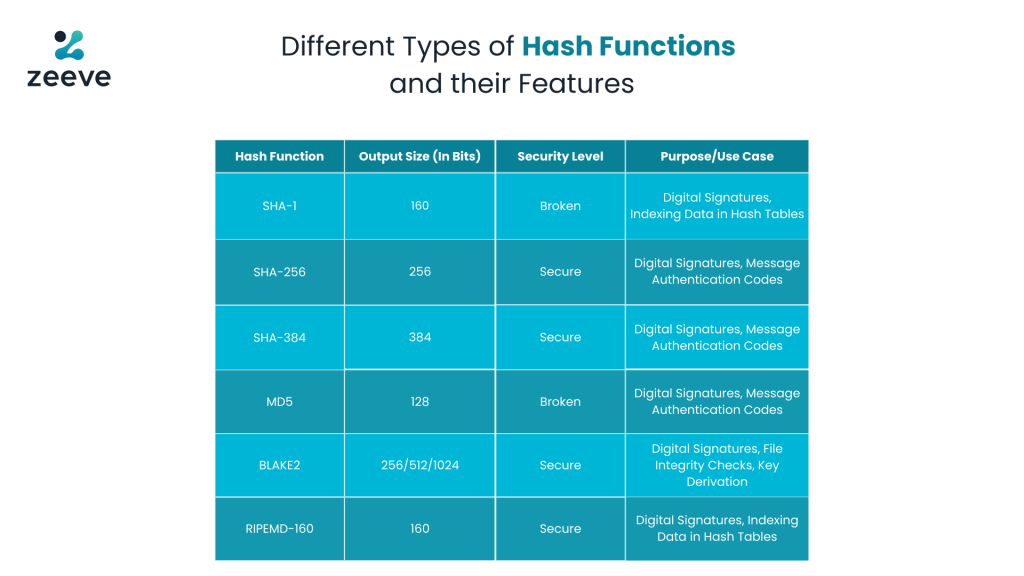
A table showing the different types of hash functions, it’s output size, security level and use cases:
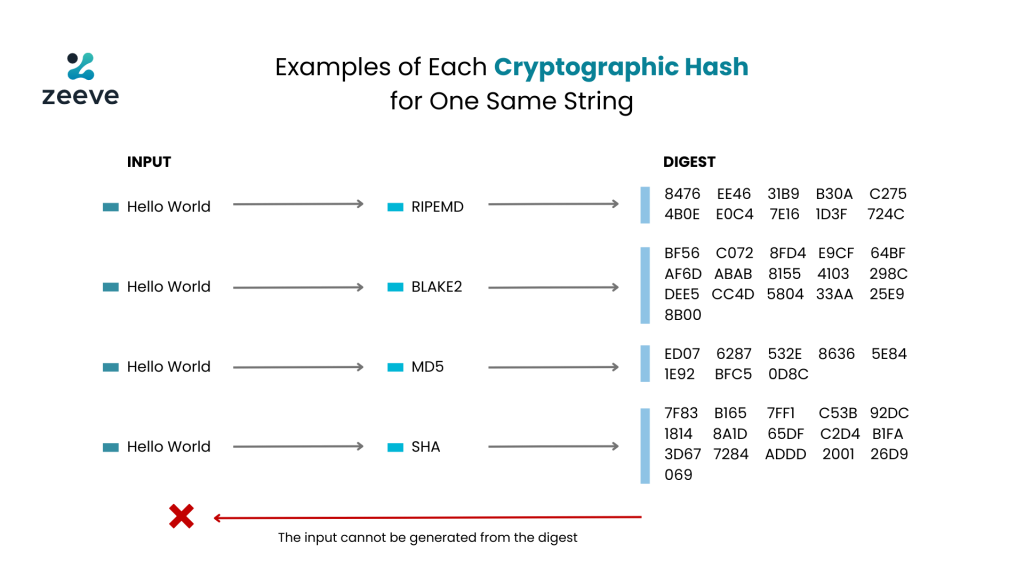
Let’s do it in practical now. Here is another infographic displaying digest for same inputs using different hashing algorithms.
Applications of Cryptographic Hash Functions
It’s not atypical to encounter cryptographic hash algorithms employed in applications such as:
Preserving Credentials
Credentials are encrypted utilizing a cryptographic hash procedure before being stored in a database. When a password’s hash value is stored instead of the actual password, the initial password is secure from pilferage.
Electronically Generated Signatures
Consisting of cryptographically hashed digital signatures can be utilized to affirm the authenticity and wholeness of electronically stored information.
Audit of Information Veracity
By evaluating the hash quantity of the dispatched information against the one derived from the source material, cryptographic hash algorithms affirm that the information has not undergone any manipulation during transmission. Should the hash values differ, it indicates that the information has undergone alteration or degradation.
Technology Derived from a Decentralized Register or Blockchain
In blockchain technology, cryptographic hash functions are employed to generate unique digital signatures for transactions. Consequently, the blockchain can be relied upon to sustain its genuineness and inalterability, rendering it a secure setting for various applications, including digital currencies.
Hashing in the context of Blockchain:
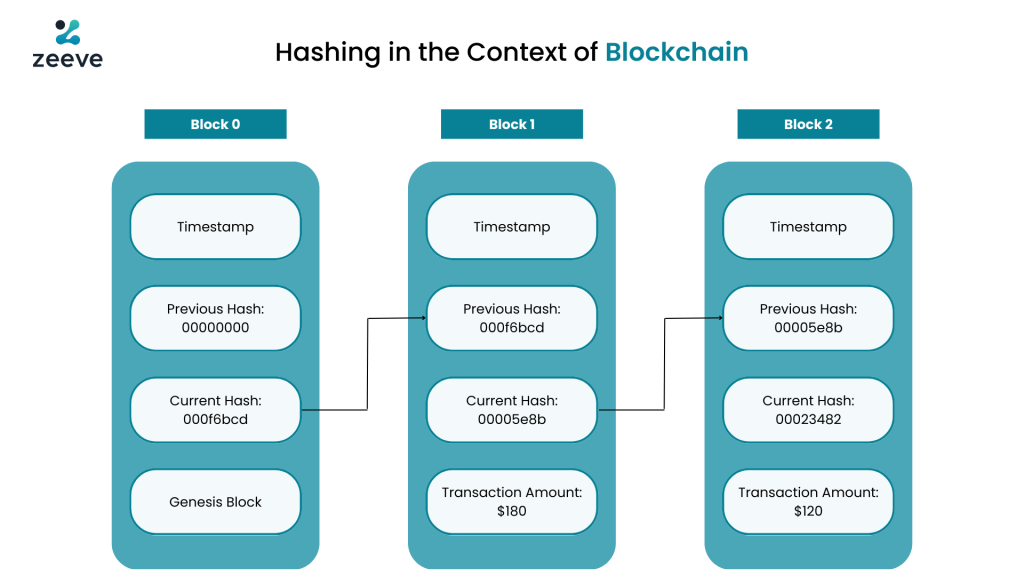
Hashing plays a critical role in ensuring the security and immutability of data in a blockchain.
Each block in the chain contains a unique hash value that is generated by applying a cryptographic hash function to the data within that block. This hash value acts as a digital fingerprint, making it easy to verify the integrity of the data within the block.
Additionally, each block contains a reference to the previous block’s hash, creating a chain of linked blocks. Any modification to the data within a block, for example in block 2, will result in a change in its hash value, which will then impact all subsequent blocks in the chain. You would need to modify all succeeding hashes if you decided to remove or add a zero in block 2, for instance. If that were the case, it would be clear if you only looked at the latest block’s hash.
Thus, the tamper-proof nature of the blockchain is maintained, as any attempt to alter any part of the chain will be easily detected through the inconsistency of the hash values.
In summary, the use of hashing in blockchain ensures that the system remains secure and trustworthy, providing a decentralized solution to storing and managing data.
Conclusion
Okay, so we have seen how hash algorithms like
SHA, MD5, BLAKE 2, and RIPEMD work, how they are used in various security applications to provide data authenticity and integrity etc.
Now, as you know hashing, don’t confuse it with Encrytion and Salting. Unlike encryption, hashing is a one-way function. You can’t reverse it to obtain the original input. This is why it’s ideal for storing passwords or other sensitive data, as the original data is never stored in plaintext. Salting, on the other hand, is a technique used in cryptography to add randomness to a hash. This helps to prevent brute force attacks.
That’s all for this edition. Stay tuned for the next thread to learn more on Cryptography, hashing and everything blockchain.