For centuries, cryptography has been a trusted technique for safeguarding sensitive information from unauthorized access.
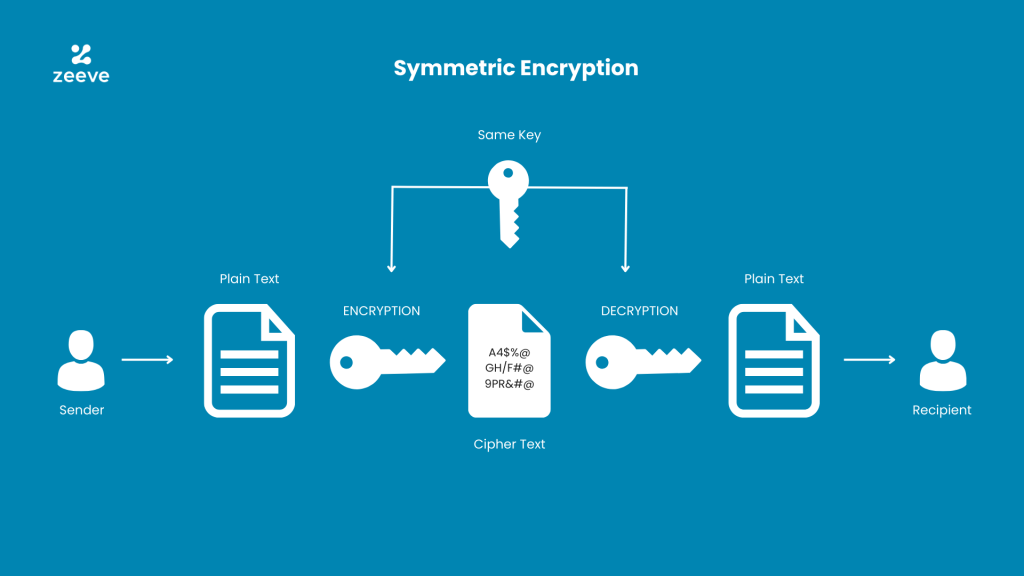
In today’s digital age, secure communication has become more crucial than ever before, and symmetric key cryptography is among the most widely used techniques for securing communication channels. This method employs a single key for both encryption and decryption of messages, making it an efficient and straightforward approach to data protection.
This article provides an in-depth exploration of the world of symmetric key cryptography, including its history, how it works, and its advantages and disadvantages. Additionally, we will discuss popular symmetric key encryption algorithms and their practical applications.
History of Symmetric Key Cryptography
Symmetric key cryptography has a rich record of using a single key for encoding and decoding from ancient cultures that employed straightforward substitution ciphers to guarantee transmissions. An instance is the Caesar ciphertext, used by Julius Caesar to speak safely with his inferiors.
In the 20th century, symmetric key cryptography progressed with the innovation of better avant-garde encryption algorithms, such as the Data Encryption Standard (DES), in the 1970s. This method was broadly utilized in public and remote sectors for secure transmission, though its short key length earned it prone to brute force invasions.
Therefore, contemporary and more protected symmetric key algorithms, such as the Advanced Encryption Standard (AES), was designed. AES was adopted as a norm by the U.S. administration in the early 2000s and puffed a longer key length, making it considerably better secure than its precursor, DES.
Symmetric key cryptography remains a commonly utilized mode for secure transmission, continually exploited in secure messaging, VPNs, and disk encryption applications.
How symmetric key cryptography operates:
Key generation
Generating keys in symmetric key cryptography necessitates the design of a private key utilized for both the encryption and decryption of data. The key must be elicited securely and protected against unauthorized entry to secure the encrypted information.
Several methods for producing symmetric keys exist, encompassing:
- Spontaneous Key Generation: This entangles creating a truly random key through a random numeral generator, causing it the most secure method as it ends the likelihood of a predictable routine in the key.
- Key Derivation: In this method, a cryptographic function generates a key from a password or another input. In this technique, applications such as disk encryption often create the encryption key by having the user input a password.
- Key Exchange: In this method, communicating companies generate and trade the key through a secure key trade protocol such as Diffie-Hellman to maintain confidentiality.
Nevertheless, it is integral to conserve the confidentiality of the key and shield it against unauthorized entry, as the security of the encrypted data relies on the key confidentiality.
Encryption
Symmetric key cryptography, encryption, and decryption use the exact confidential key. The cryptographic procedure operates as follows:
- The cryptographic algorithm obtains an unencrypted transmission and the private key.
- The cryptographic algorithm transforms the unencrypted transmission into a coded message by performing mathematical processes and modifications based on the private key.
- The resulting coded message is a scrambled rendition of the source information, making it impenetrable to anyone without the secret key.
- The cryptographic operation in personal key cryptography provides privacy by causing the information to be indecipherable to anyone without the private key. The private key must be kept secure and imparted between the sender and recipient to ensure the confidentiality of the communication.
Transmission
Since the key must be disseminated confidentially between the transmitter and the recipient for the likeness to be secure, there are several routes to share symmetric keys:
- Key Interchange Routines: These cryptographic patterns permit two parties to establish a secret key over an insecure transmission medium. Examples include the Diffie-Hellman key exchange and Elliptic Curve Diffie-Hellman (ECDH).
- Key Dissemination Centers (KDCs) rely upon third-party systems that confidentially disperse keys to users. Illustrations include Kerberos and Secure Naming.
- Out-of-Band Communication: This is a way of disseminating the key over a different transmission channel, such as a phone call or face-to-face meeting, guaranteeing its secure transmission.
- Key Repository: This is a method where a delegated third party securely stores the encryption key and can recover it in an emergency.
Irrespective of the procedure utilized, it’s crucial to secure the confidentiality of the key transmission because a compromised key can usher in the loss of privacy and the virtue of the encrypted information.
Decryption
In symmetric key cryptography, the recipient utilizes the secret key to decipher the encrypted transmission and recover the source’s clear text. The reversal procedure of encryption involves the decryption process.
Here is a broad outline of the inverse operation:
- Obtain the encrypted message: The recipient obtains the encrypted correspondence from the transmitter.
- Employ the secret Key: The recipient employs the private key, previously disseminated with the transmitter, to decipher the encrypted message.
- Implement the decryption routine: The recipient executes the same inverse procedure the transmitter utilizes to encrypt the clear text. This routine employs the secret key to undo the encryption operation.
- Secure the clear text: The recipient obtains the original clear text after executing the inverse procedure on the encrypted message.
It is important to point out that symmetric key cryptography necessitates that both the transmitter and the recipient possess the exact confidential key. If the key is misplaced or becomes endangered, the encrypted messages will not be able to be deciphered, compromising the privacy of the transmission.
Examples of Symmetric Key Cryptography Algorithms
The following are some examples of symmetric key cryptography algorithms:
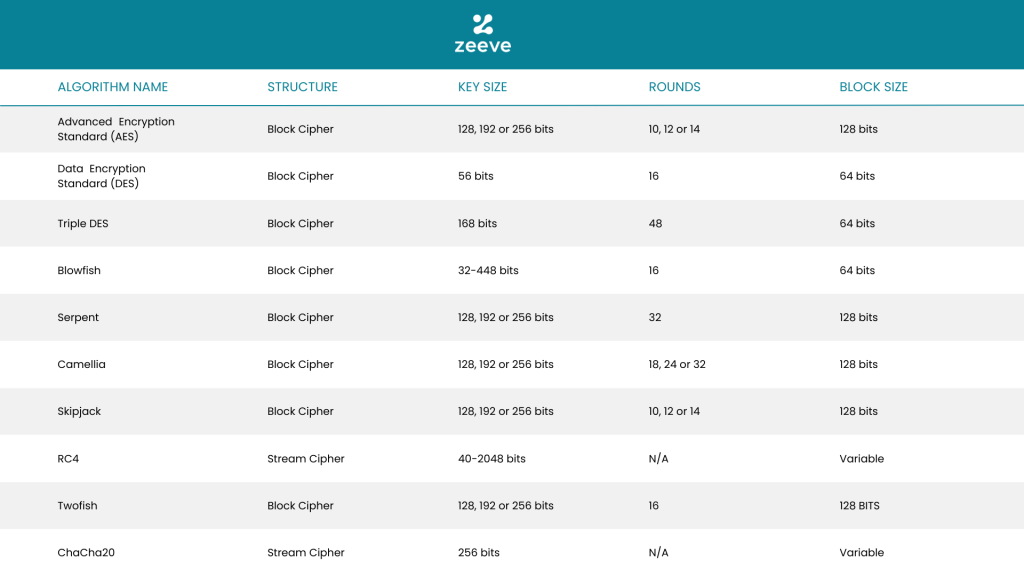
Advanced Encryption Standard (AES)
AES is a symmetric key encryption algorithm that is widely used in securing data. It was adopted by the US government in 2001 and is considered to be one of the most secure encryption algorithms available. AES uses a block cipher with a key length of 128, 192, or 256 bits.
Blowfish
Blowfish is a symmetric key encryption algorithm that was designed by Bruce Schneier in 1993. It uses a block cipher with a variable key length of up to 448 bits. Blowfish is considered to be a fast encryption algorithm and is often used in secure communication protocols.
Data Encryption Standard (DES)
DES is a symmetric key encryption algorithm that was developed by IBM in the 1970s. It uses a block cipher with a fixed key length of 56 bits. DES is no longer considered secure and has been replaced by AES in many applications.
Triple DES
Triple DES is a variant of DES that uses three rounds of encryption to provide greater security. It uses a block cipher with a key length of 168 bits.
Rivest Cipher 4 (RC4)
RC4 is a symmetric key encryption algorithm that was designed by Ron Rivest in 1987. It uses a variable key length of up to 2048 bits and is often used in secure communication protocols such as SSL and WEP.
ChaCha20
ChaCha20 is a symmetric key encryption algorithm that was designed by Daniel J. Bernstein in 2008. It uses a stream cipher with a key length of 256 bits and is considered to be a fast and secure encryption algorithm.
Serpent
Serpent is a symmetric key encryption algorithm that was one of the finalists in the Advanced Encryption Standard (AES) competition. It uses a block cipher with a key length of 128, 192, or 256 bits and is considered to be a very secure encryption algorithm.
Twofish
Twofish is a symmetric key encryption algorithm that was designed by Bruce Schneier in 1998. It uses a block cipher with a key length of up to 256 bits and is considered to be a fast and secure encryption algorithm.
Camellia
Camellia is a symmetric key encryption algorithm that was developed jointly by Mitsubishi Electric and NTT of Japan. It uses a block cipher with a key length of 128, 192, or 256 bits and is considered to be a very secure encryption algorithm.
Skipjack
Skipjack is a symmetric key encryption algorithm that was developed by the US government in the 1990s. It uses a block cipher with a fixed key length of 80 bits and is no longer considered secure.
This table summarize everything:
Benefits and drawbacks
Benefits
Advantages of Symmetric Key Cryptography:
- Speed: Symmetric key cryptography is more instantaneous than other forms of encryption, making it applicable to large amounts of data.
- The comfort of Use: Symmetric key cryptography is fairly simple to implement, making it accessible to many users.
- Expense Effective: Symmetric key cryptography needs minor processing capacity and storage than other encryption setups, making it a cost-effective answer.
- Strong Security: Symmetric key cryptography delivers strong security, making it appropriate for applications mandating high tiers of security.
- Flexibility: Symmetric key cryptography can be used with many algorithms, making it a flexible solution.
- Scalability: Symmetric key cryptography can be utilized for small and large data batches, making it a scalable answer for different applications.
- Key Management: Symmetric key cryptography utilizes a single key, making key management easier than other encryption setups.
- Versatility: Numerous applications, incorporating secure file transfers, VPNs, and secure email services, can use symmetric key cryptography
Drawbacks
Impediments of Symmetric Key Cryptography:
- Key Distribution: The challenge of securely disseminating the key to the groups concerned in the transmission can be a principal disadvantage of symmetric key cryptography.
- Key Compromise: If the key is misplaced or stolen, the security of the transmission is compromised, making symmetric key cryptography helpless to attacks.
- Fixed key Strength: The length of the key utilized boundaries the strength of symmetric key cryptography. Stronger protection results from lengthier keys, but longer ones require more processing capacity and storage.
- Single Key Restriction: Symmetric key cryptography requires both groups to access the exact key, making it inappropriate for multi-party contact.
- Susceptibility to Brute-Force Attacks: An attacker can execute a brute-force attack on symmetric key cryptography by attempting all likely keys until they find the right one. This attack can be successful if the key is short or the assailant has access to powerful computing resources.
- Security concerns: One of the primary safety worries related to symmetric key cryptography is the danger of key subversion. If attackers intercept or procure the key, they can effortlessly decode any encrypted data, exposing delicate information. This danger can be alleviated by employing secure key exchange methods, such as public key cryptography, to allocate the key securely.
Real-life application of symmetric key cryptography
Unique Uses of Symmetric Key Cryptography:
- Data in Transit Scrambling: Symmetric key cryptography is often employed to scramble data during transmission over networks, such as in SSL/TLS protocols for securing web communications.
- Data at rest Scrambling: Symmetric key cryptography can also scramble data stored on disks or other storage gadgets, protecting against unauthorized access.
- Disk Scrambling: Multiple operating systems, such as Microsoft Windows and Apple macOS, use symmetric key cryptography to scramble the whole disk, protecting the stored data in the occurrence of loss or theft of the device.
- Virtual Private Networks (VPNs): VPNs constantly use symmetric key cryptography to scramble data transmitted over the Internet, providing secure remote access for users.
- Mobile Correspondence: Symmetric key cryptography is utilized in various mobile correspondence protocols, such as iMessage, to deliver certain end-to-end correspondence.
- File Contraction: Some file contraction formats, such as ZIP, use symmetric key cryptography to provide additional safety for compressed files.
Conclusion
Symmetric key cryptography constitutes a crucial facet of modern cyber protection and is habitually employed to protect delicate data. The primary benefit of symmetric key cryptography lies in its speed and proficiency, rendering it fit to encrypt significant amounts of information. Keeping the encryption key unknown ensures its relative security.
Nonetheless, symmetric key cryptography harbors some drawbacks, such as the condition for both parties to possess a duplicate of the key and the probability of data depletion if the key is misplaced or stolen. Despite these impediments, symmetric key cryptography stays a vital and effective tool for safeguarding sensitive information in numerous applications.
In essence, symmetric key cryptography is a useful and capable method of encryption that plays a substantial role in modern cybersecurity.
You can also read about blockchain technology here.