Specific projects while using the public or permissive blockchain unequivocally face an imminent challenge of standardization because of the existing tech stacks that public and permissive blockchains use. To deal with this issue, appchains engineered an innovative way forward through application specific chains having their own consensus model to support such projects. However, while doing so, these app-chains exposed points of failure, nonetheless in the form of: Composability & Security.
How?
Since the applications developed resided within the walled gardens of specific use-cases and network effects, other solutions were heterogeneous and couldn’t reside on the same network. This created a point of failure on appchains where clustering of validation could compromise the network
Why?
App-chains have their own consensus mechanisms making their ecosystem non-incentivizing for other networks to participate and secure the ecosystem. Due to this reason, app-chains experienced node validation problems. For applications to survive on app-chains, they need assurity of security for its users.
What is a Replicated Security Model?
Replicated Security is an extended security layer that appchains can use to inherit the security features of the provider chain to safeguard their network. The provider chain shall charge a percentage of fees for validating the transactions and safeguarding the network from abuse.
How the Replicated Security Model Works?
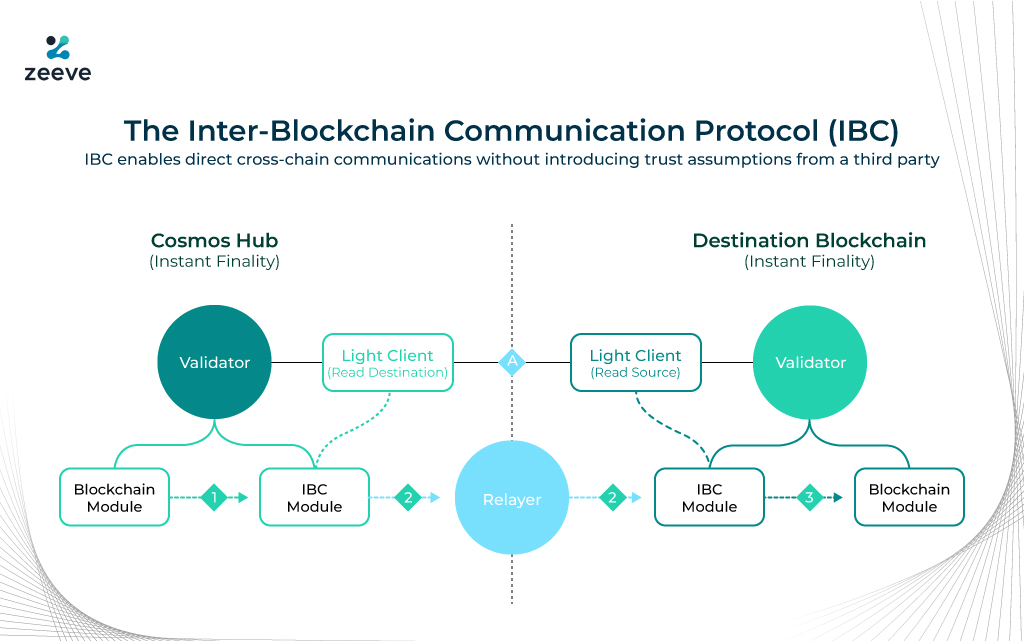
Using the RS formerly known as ICS or Interchain Security, the Cosmos Hub works as a provider to the consumer chain/app chain. It uses the IBC or Inter-Blockchain Communication (IBC) protocol for connecting and validating the transactions of the consumer chain through data packets which are relayed from the provider chain to the consumer chain in the following manner as explained in this image;
How This Model Establishes Security Concepts?
Like, we already touched upon in the starting of this article that appchains have walled operations. As a result, when you have a walled tech architecture, it amounts to a handful of validators to validate the system and receive incentives in return. However, such a practice is impractical because the validators can choose to act rogue if the transcations value outsmarts the rewards accrued. Replicated Security Model provides a trade-off to such applications where they can relay the block data to the IBC which publishes the information across various nodes. In doing so, it protects the network against point of failures because the attacker must compromise all the validating nodes that are rendering security to the application chain through the RS model to compromise the network. Since the provider chain has other clients and node validators are distributed evenly, it completely discourages such pursuits.
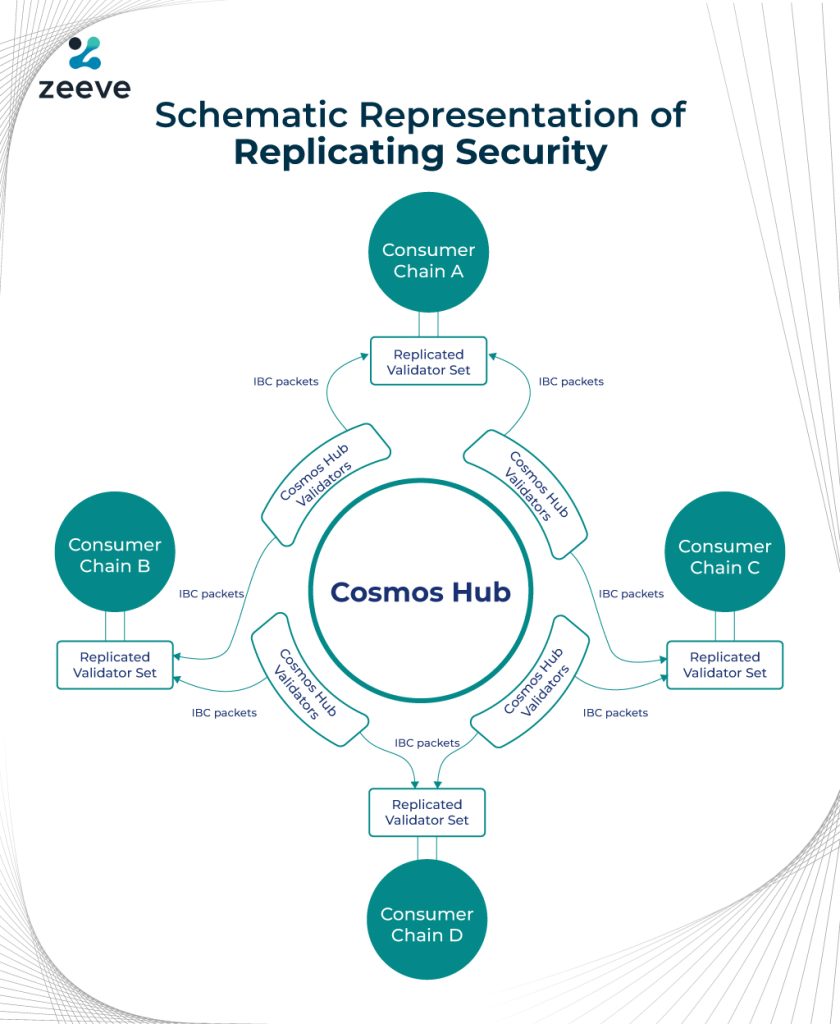
How the Replicated Security Model Would Help the Cosmos Hub App Chain Ecosystem?
Cosmos Hub provides IBC, which creates a symbiotic relationship with the partner networks/consumer chain to replicate the security of the Cosmos Hub. In order to do that, the Cosmos Hub uses Practical Hub Minimalism which minimizes the working features of the consumer chain to negate the point of failures. But, in doing so, the Cosmos Hub shall be monetizing the trade-off lent through its network to the consumer chains/network, thereby solving the Cosmos appchain validator problem.
Moreover, the Practical Hub Minimalism has been designed keeping in mind conflicts of interests of the user-groups and mediating through a trustless decentralized manner to resolve issues, if they happen at any point of time. In this way, the Cosmos Hub shall maintain neutrality and minimalism to secure the network from grounds-up and cater to the Cosmos Appchan Validators. Here’s how the entire process of safeguarding the Cosmos appchain validator would appear like;
Who all are Using the Cosmos Hub Replicated Security Systems?
At the time of writing, the Cosmos Hub has already onboarded Neutron, which is DeFi smart-contract platform to address problems like providing cheaper transaction gas to scale the ecosystem. In addition to this, Neutron also helps in trading and swapping digital assets on its ecosystem.
Since Neutron is built using Tendermint and CosmoSDX, it is highly composable with other applications as well. Neutron’s security aspects are modeled using the game theory where sustaining the network would make ATOM more valuable and if the network is resilient against attacks and hacks, it will safeguard the Neutron ecosystem. So, it creates a win-win situation for both the parties. In addition to this, Neutron has also expressed the intent to sponsor the ecosystem and build the same from ground up so that every community from the IBC can participate and protect the ecosystem. The long term trade-offs seem promising for the Cosmos Hub to provide the security layer to app-chains, which is the need of the hour for them.
Let’s Build an app-chain using Cosmos SDK & Zeeve:
If you are planning to build a Cosmos SDK chain, we can help. Zeeve simplifies the development using Cosmos SDK with plug and play developer tools and Zeeve Managed infrastructure support. Running a production-ready standalone blockchain demands more than just a set of nodes, you need explorers, faucets, data indexing protocol, cloud flexibility and even migration support to aapchain infrastructure.
Zeeve makes sure you get everything under one roof and can move to production with minimal turnaround time. Need more information? Get in touch with our blockchain experts and see how Zeeve can simplify your Cosmos SDK based development experience.