Personal chats, pictures and videos data are stored on centralized servers. As a result, central servers could see what has been contained in the message. But end-to-end encryption safeguards against such odds by giving complete privacy while using a third -party platform for messaging. In this article, we shall dive deep to learn about End to End Encryption and its various associated factors and benefits that make it safe when it comes to safeguarding privacy and maintaining safety.
What is End to End Encryption?
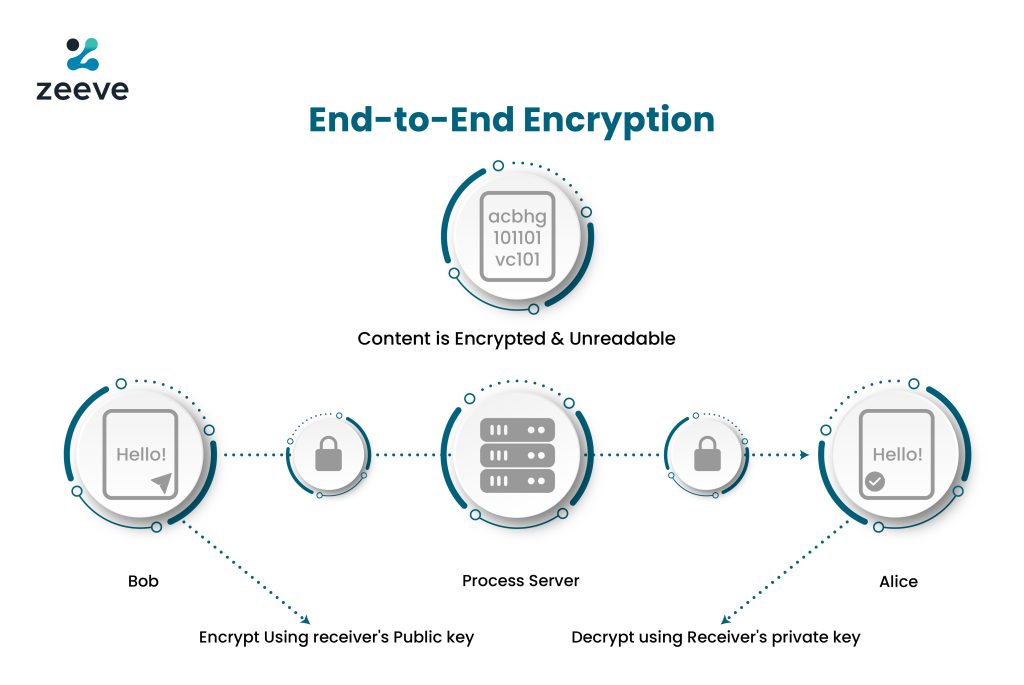
End-to-End Encryption or E2EE is a secure method of communication where the third party, which is hosting the platform to trigger the exchange of information, cannot read the information in plaintexts.
To put that into perspective, supposedly, if you are Bob and you are sending an information to your friend Alice, “Meet Me at 4PM at Starbucks on 12th ELM Street in London”, the platforms shall be encrypting the message like this in cipher-texts “^&*%$##@@$^HHGGFDL^^%%$$##PMMN”:LK}}}}SWRETH>><<MMCXSA@@VIK” and when this message is received by Alice, it gets converted into plain text as “Meet Me at 4PM at Starbucks on 12th ELM Street in London.”
How Does End-to-End Encryption Work?
At the end points of the receiver and the sender, the cryptographic keys are placed which helps in decrypting the ciphertext into plaintexts every time a message has been exchanged.
In this model, public key cryptography is used or also known as asymmetric cryptography. The process goes in the following ways:
The server or the intermediary shall be involved in sharing the message with the immediate peer. Generally the intermediary will be a server, which shall belong to an ISP, aka Telecom Service Provider. Since a public key cryptography is in use, the intermediary, which is the company, cannot intervene in the private messaging.
In order to achieve that, the recipient creates a public key and embed the same in a digitally signed certificate, which is recognized by a Certificate Authority (CA). The CA makes the Public Key (PK) public by widely distributing the same across channels. Once the CA distributes the PK, the message decrypted by the PK becomes authentic. However, the CA shall obstruct or reject those certificates with a different PK but by the same name. Hence completely safeguarding the flow of information across channels and peers.
Where is End to End Encryption Mostly Used?
End to end Encryption set-up is widely acceptable in all those business frameworks where data protection is an essential element like in finance, healthcare and communication.
Companies which are wishful of complying with the GDPR guidelines and other basic privacy issues resort to using E2EE encryption.
For example, messaging apps like Whatsapp use E2EE and POS stores rely on E2EE to protect user’s data. In this way, they safeguard users from any potential point of failure.
How Does End to End Encryption Differ From Other Types of Encryption?
End to End Encryption provides asymmetric encryption, which means, only the sender and the receiver can encrypt and decrypt the message using a private key, which could be a password, code or string of randomly generated numbers. Whereas, in other forms of encryption like Encryption in Transit, the hosting server decrypts the message and encrypts it again to send it to the receiver. As a result of that, it creates potential points of failures or vulnerabilities.
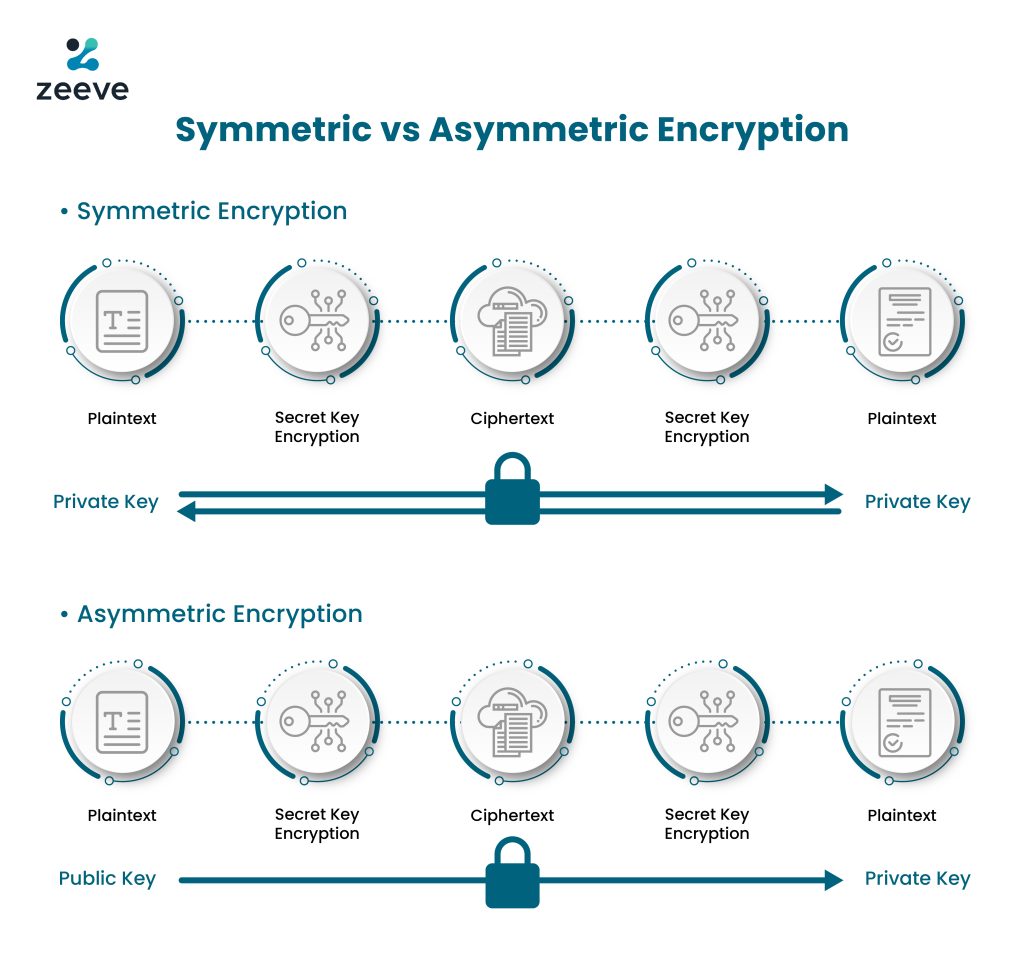
How Such a Feature of the End to End Encryption Makes It Blockchain Compatible?
End to End Encryption introduces asymmetric encryption where you need the private key pairs to decode the public keys. In the absence of asymmetric key cryptography, the blockchains would have had no choice but to rely on symmetric encryption. Symmetric encryption would have led to a common key sharing between trusted parties which would have ideally negated the principles of blockchain that relies on decentralization. However, when E2EE comes into play, it introduces private key cryptography where you have an open public key for all but to execute any action on that public key, you need a private key that acts as a digital signature for the users to execute functions.
Why is End to End Encryption Important?
Average cost of data breach is USD 3.86 million. Whereas, if you take into account only the United States, the amount stands at a whopping USD 8.64 million.
That said, it creates major vulnerabilities for enterprises and businesses to function. Through End to End Encryption, a user-authorized access can be guaranteed to put complete control over how the data has been used. With the use of a centralized key management system that follows key management interoperability protocol, enterprises can function with a peace of mind and ensure complete protection and privacy to its users.
What End to End Encryption Protects Against?
Prying Eyes: The intermediary has no role to play in the communication and they can see the information only in ciphertexts. Hence it protects against prying eyes.
Tampering: As the message is readable in ciphertexts, it means that the participating intermediary cannot tamper with the message. Hence it provides complete security and protection.
Potential Point of Failures of End to End Encryption
MetaData: Though you have concealed the message inside the certificate, it is very hard to hide the date and time and the recipients of the message. As a result of this, the malicious actors know whom to hit and at what time to compromise the message. Hence making the system not completely water-tight from a security standpoint.
Compromised Endpoints: There’s a greater chance of the attacker to compromise the model at endpoints. Once the attacker does that, he/she can trigger the man-in-the-middle attack with the compromised public keys.
Intermediaries In Crime: Oftentimes, it might be very hard to judge whether the intermediary is providing E2EE or Encryption in Transit. If they are providing Encryption in Transit on the pretext of E2EE, your data is vulnerable to compromises at multiple checkpoints.
How to Overcome the Odds?
To overcome the odd, one can look forward to homomorphic encryption which allows computation to happen on the texts without decrypting the same. Hence providing a perfect solution to computing sensitive information without leaving any trace of data behind.
In our next coverage, we shall explain in detail about homomorphic encryption and how it can solve the problems left behind by E2EE.